Do you need advanced security options?
You've already installed a password manager and turned on 2-factor authentication. Do you need to do more?

Can you make yourself safer online by finding the giant ONLINE SECURITY dial and turning it to 11 or beyond? Sadly, no.
Security isn’t an ingredient you add to your devices. There’s no set-it-and-forget-it combination of magical software and hardware that will repel evildoers with an impenetrable force field.
Security is a process, not a product. There are indeed best practices you can follow, and tools you can use to make it easier to avoid making easy mistakes. If you’ve followed the advice I laid out previously in this series, you’re already much of the way there: You’ve identified your most important online sites and services and ensured that access to the data in those locations is protected with strong, unique passwords; you’ve installed a password manager to make the process of signing in easier and more secure; and you’ve added multi-factor authentication (aka 2-factor authentication or 2FA) wherever possible.
This is the conclusion of a four-part series. If you missed the earlier installments, you can catch up here:
- Introduction: “Getting your online security in order”
- Part 1: “Get your passwords organized (in 30 minutes or less)”
- Part 2: “How to choose (and use) a password manager”
- Part 3: “Multi-factor authentication is easier than you think”
Is that enough? Do you need to do more? As any security professional will tell you, the answer to that question is a firm, “Well, it depends.” Depends on what? You can decide for yourself by looking at your personal threat landscape. Specifically, by asking two questions.
Which types of security incidents am I most likely to encounter, and how can I minimize their impact?
This one’s pretty easy. Data breaches are still routine; and if my inbox is any indication, phishing attacks and garden-variety malicious software (often delivered by email attachments) are still endemic. These days, one of the most common threats I see is pure social engineering. I must get two dozen emails every week thanking me for my $400+ Geek Squad renewal and offering a toll-free number to call if I want to cancel my membership and keep my credit card from being charged. It’s a scam, of course. (The U.S. Federal Trade Commission has a good write-up.) The goal is to get you on the phone so they can trick you into handing over your credit card or bank account details ("to process the refund,” of course) or trick you into allowing remote access to your PC.
And it’s not just Geek Squad that gets this treatment. Here’s one I received last week, ostensibly from McAfee:
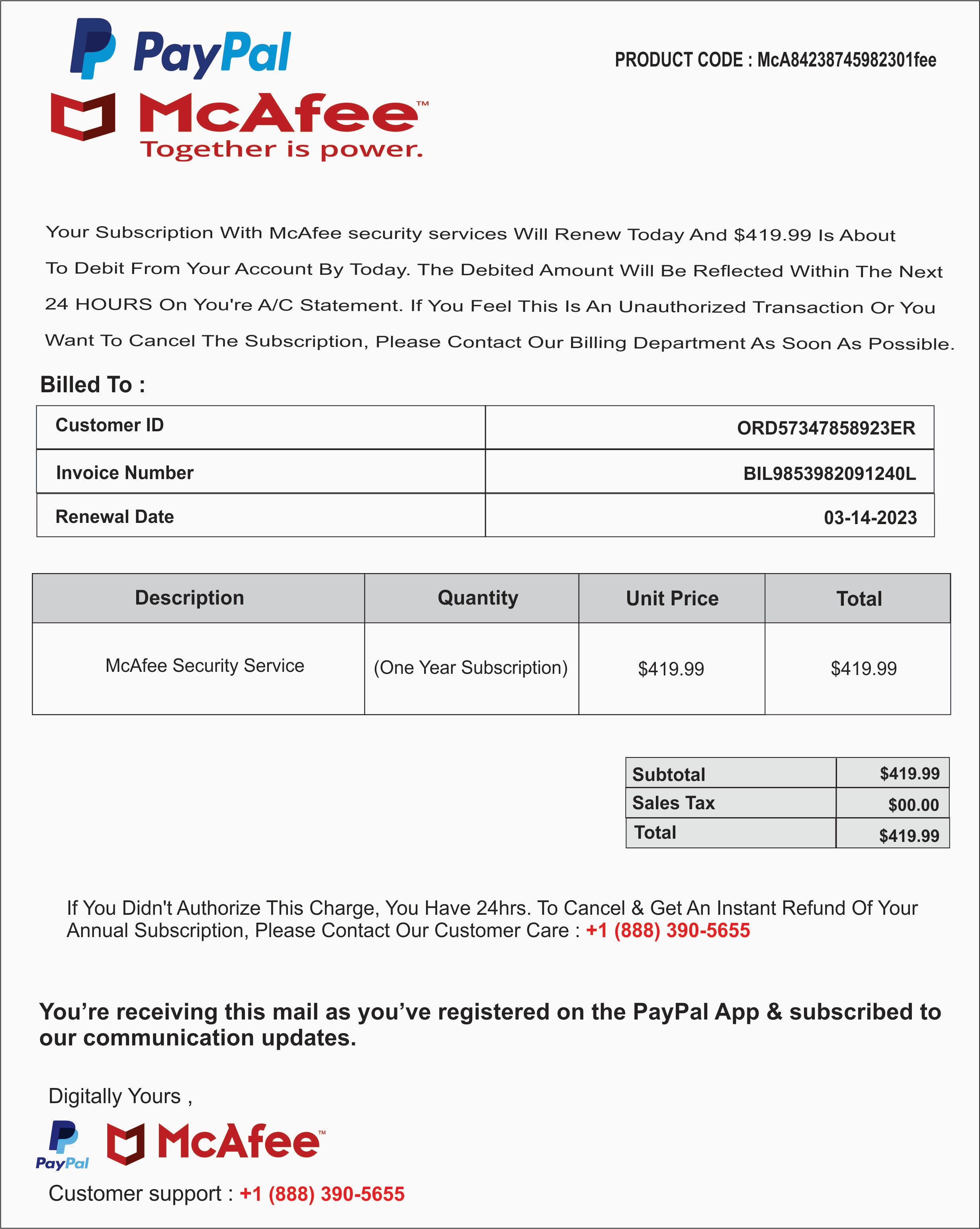
Basic security precautions—a password manager, 2FA, and the common sense to ignore/delete anything that looks like a scam—will protect you from all those threats.
The second question is a little tougher.
What are the worst security incidents that can happen to me, and how likely are they to occur?
People who work in businesses that are likely to be targeted by malicious and persistent actors (banking, defense, journalism, political activism, and so on) should think long and hard about this one. You don’t even need to use your imagination, because there are plenty of real-world examples to draw from.
Even if you’re not a likely target of elite hackers, you still might have some things to worry about. If your business depends on the web for its continued operation, for example, you should definitely take precautions to avoid being impacted by ransomware. Similarly, if you regularly use online banking services to send and receive money, you need to put precautions in place to avoid being scammed. The most important layer of protection in all of those cases involves training people (including yourself!) to recognize potential threats.
If you’re not in one of those groups, you probably don’t need to take extraordinary precautions. Pay attention to the basics and you’ll be fine.
With that assessment complete, let’s look at some questions people regularly ask of me.
Do I need a third-party antivirus program or advanced security software?
For most people, on most platforms, the built-in security software is good enough. On PCs running Windows 10 or Windows 11, which are historically the most likely to be targeted by malicious software, the built-in Microsoft Defender Antivirus offers sufficient protection.
Ironically, third-party developers that charge for security software and services have in recent years become essentially scareware purveyors, warning of vague “threats” that require a paid subscription to neutralize. If you are concerned that you might have encountered something malicious online and want a second opinion, the free version of Malwarebytes is safe for a quick scan. You can run it without having to install it and have it run permanently in the background.
Medium and large businesses that have security personnel on staff (or on call) might benefit from enterprise security software that can identify threats to the network. But individuals and small businesses don’t need this level of protection.
How do I know which sites offer 2-factor authentication?
If you use 1Password, you can check the WatchTower pane to identify sites where you’ve saved passwords that also offer multi-factor authentication.
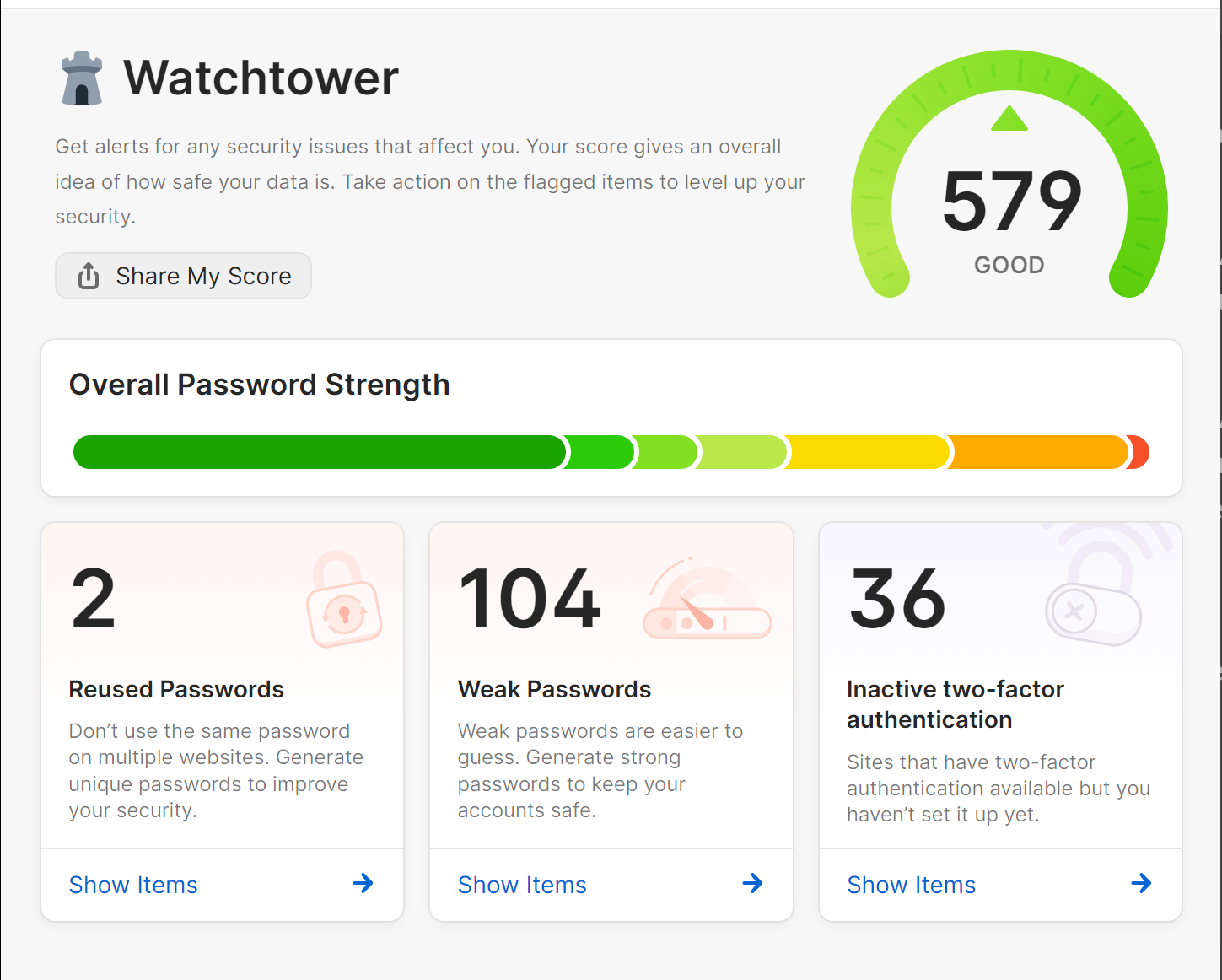
You’ll also find a useful open-source directory of sites, organized by category, at 2fa.directory.
Is it safe to use my password manager for 2-factor authentication?
Well, that depends.
Most modern password managers—including the two I recommend, 1Password and Bitwarden—allow you to generate authenticator-style Time-based One-Time Password (TOTP) codes directly from the password manager. That’s tremendously convenient, because it means you don’t have to keep checking your mobile phone and manually typing in codes when required. It also means those encryption keys are synced to other devices so you don’t have to worry about being locked out of key accounts if you lose your phone.
The flip side is that it means an attacker who successfully steals and decrypts your password vault has access to everything. If you’ve chosen a strong master password and you have 2-factor authentication turned on for your password manager (using a security key or a separate authenticator app), that risk is very small. But it’s not zero.
I’ve adopted a hybrid approach that satisfies my requirements. I use a third-party authenticator app and hardware keys for services that I consider critical (including my password manager), while allowing my password manager to handle codes for less crucial sites.
Is it possible to remove passwords completely?
An emerging technology called passkeys offers the potential to authenticate you to sites and services without ever having to use a password. When you’re asked to sign in, you approve the request by using a biometric proof or PIN on a hardware device that’s already conclusively tied to your identity, such as a phone, a computer, or a hardware security key. The FIDO Alliance has a useful explainer.
Passkeys can be synced between devices in the same way as password managers sync an encrypted password vault.
This technology is still emerging, but you can take advantage of it already if you have a Microsoft account. You’ll need to install the Microsoft Authenticator app and then follow these instructions to remove the password from your account: “How to go passwordless with your Microsoft Account.”
Passkey support is also available from Apple using an iPhone and the iCloud Keychain. For instructions, see this article: “Sign in with passkeys on iPhone.”
Google’s support for passkeys is still emerging. It’s fully supported on Android devices using Google Password Manager, but integration with Windows and MacOS devices is a little tricker. Details are in this article: “Passkey support on Android and Chrome.”
Any questions? Feel free to leave them in the comments below.
Read the entire series
Introduction: “Getting your online security in order”
Part 1: “Get your passwords organized (in 30 minutes or less)”
Part 2: “How to choose (and use) a password manager”
Part 3: “Multi-factor authentication is easier than you think”