Multi-factor authentication is easier than you think
Having a strong, unique password is a good start, but it's not enough. Adding a second layer of protection is worth the extra effort.

In Part 1 of this series, you took an important step in tightening up your online security by identifying the online accounts that are most important to you and creating strong, unique passwords for each one.
That’s a good start, but simply requiring a password to access an online account is not nearly enough to prevent disaster. If an unauthorized person gets ahold of that password, they have full access to your account and everything in it.
How can that happen? Let us count the ways:
- A data breach at the service provider can expose user names and passwords. If you’re in the habit of reusing passwords, as too many people are, a breach at an unrelated site can make it possible for an attacker to access any account that uses those credentials.
- If you’re fooled by a phishing email, you might unknowingly turn over your user name and password to an attacker.
- A vulnerability in otherwise innocent software can result in a keylogger (or other forms of malicious software) being installed on your PC. (That’s the method used by attackers who breached servers containing LastPass user data. And note that the engineer who was targeted in that attack should never have been accessing such sensitive resources from a computer running personal software.)
- And when all else fails, there’s the good ol’ brute force attack, in which a bad guy just keeps trying to sign in using different passwords until he finds one that works. This method is extremely effective against users who use passwords that are almost identical.
The solution is to set up each online account so that a password alone isn’t sufficient to sign in on a device you’ve never used before. In that case, the website looks at the attempted login and says, “Hmmm, I don’t recognize this device. You need to provide one additional piece of identification before I allow you to sign in.”
That’s the principle behind multi-factor authentication, also known as 2-factor authentication (2FA) or two-step verification. If the person who pilfered your password doesn’t have that additional piece of identification, they won’t be able to sign in.
What can you use to establish your identity in a way that won’t be easily available to a stranger? Here are the most common options, in increasing order of security:
SMS/email
After you enter your password, the server sends an SMS text message containing a one-time password (typically a numeric code, although some sites use a combination of alphanumeric characters) to a phone number or email address you’ve previously registered as belonging to you. If you enter the code correctly, you’re allowed to finish signing in. If you can’t provide the code, the sign-in attempt is denied.
This method has the advantage of being easiest to use. It doesn’t require any setup behind providing a phone number or email address as part of the profile you create when you sign in to the account. It’s possible for a determined attacker to work around this form of authentication, which means it’s inappropriate for anyone who has a high risk of being targeted by criminals or state-sponsored intelligence agencies. But it’s incredibly effective for anyone who doesn’t fall into those groups.
Authenticator app
Using this method, you’re required to enter your password and then confirm your identity by entering a numeric code generated by an app running on your smartphone. For each site that supports this type of authentication, there’s a one-time setup process that requires entering a secret encryption key (usually by scanning a QR code, although you can also manually type or paste the key). The app uses that secret key and the current time to generate a time-based one-time password (TOTP).
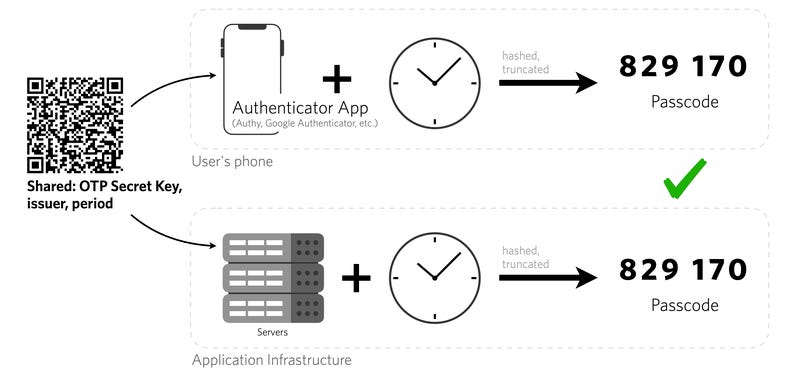
Because the TOTP format is based on the widely used Internet Engineering Task Force (IETF) standard RFC 6238, you can use any authenticator app to generate these codes. Google Authenticator is popular and works on Android and iOS devices. Google’s app works on one device at a time and requires you to export codes from your old phone if you upgrade to a new device; if your phone is lost or damaged, that can leave you in an awkward bind.
I prefer the Microsoft Authenticator app, because it works on multiple devices and supports easy backups. The third-party Authy app, developed by Twilio, also allows backups and is well supported. An increasing number of password managers now integrate TOTP support directly, which means you can fill in passwords and supply 2FA codes seamlessly, without having to check a smartphone app, and the encryption keys are automatically backed up along with your passwords. The list of password managers that support this feature includes 1Password, Bitwarden, and RoboForm. (Here, for example, are the instructions for using 1Password to generate TOTP codes: “Use 1Password as an authenticator for sites with two-factor authentication.”)
Hardware security key
A hardware security key connects to a device directly, through a USB port, a Lightning port, or an NFC connection. Not every service supports hardware keys, but if you find one that does, you can set up a key to serve as a second authentication factor. Typically, that means inserting the key into the device, entering a PIN (which you create), and then tapping the device to activate it.

Its nearly impossible for a remote attacker to spoof a security key, but the fact that this is a small hardware device means that it suffers from an inevitable weakness: If you lose it, you risk being locked out of your account completely. That’s why most security experts recommend that you configure a backup security key in case the primary key is lost or damaged.
Hardware keys aren’t cheap. Yubico keys, which are among the most popular, typically cost $50 and up. I’ve had good luck with a much less expensive model from TrustKey that, alas, is not currently available from Amazon. (Update: That TrustKey T110 is back in stock and only $18.99. I recommend it.*) Whichever one you buy, make sure it supports the FIDO2 standard, which will allow you to continue using it as passwordless authentication standards evolve.
Token device
These specialized devices are single-purpose pieces of hardware that generate one-time passwords the same way an authenticator app does. Typically, these devices are used for high-security services, such as banking, where the extra hassle of using a hardware device is a feature, not an inconvenience. For mere mortals, not so much.
So, which 2FA option is right for you?
Let me put this as bluntly as possible: Any 2FA option is better than none. Period, full stop.
Yes, SMS text messages are easier to compromise than other forms of authentication, but that usually requires a degree of targeting that isn’t relevant to the average person trying to keep their checking account and credit cards secure.
If you’re not intimidated by technology, switching to an authenticator app and turning off SMS authentication where possible is a good way to tighten security. But if you’re just trying to help mildly technophobic friends and family members, keep it simple and encourage them to use whatever works.
For those in extremely sensitive jobs, or anyone working in opposition to an authoritarian government anywhere in the world, the stakes are much higher. Whenever possible, you should turn off SMS authentication options and use hardware security keys to enforce maximum security. And even then, you have a right to be paranoid. Just look at what happened to Jamal Khashoggi, who died as the direct result of his phone being hacked by some of the most aggressive spyware imaginable.
Save your backup codes
Any effective security precaution comes with a built-in risk. If it’s good enough to keep out the bad guys, it’s capable of locking you out, too. And if there’s a magic back door that can allow you back in, well, the bad guys can certainly figure out a way to exploit that back door.
So, when (not if) you enable multi-factor authentication, the single most important thing you can do is to create and print out backup recovery codes for every site where you enable this option. Every site that supports 2FA includes an option to create and save recovery codes. Some sites allow you to create one and only one code. Others allow 10 codes. Whatever the details, it is crucial that you save those codes in a place where you can get to them if your normal 2FA option suddenly disappears.
The simplest way to save those recovery codes is the old-school option: Print them out, on paper, and throw that printout into a folder in a locked file cabinet. As an alternative, you can save them as text or PDF files in a cloud storage service. Just make sure that service is accessible in the event your 2FA option goes south.
Coming next week: How I manage my online security, plus advice on how to set up 2FA for popular sites and some bonus password manager tips.
Read the entire series
Introduction: “Getting your online security in order”
Part 1: “Get your passwords organized (in 30 minutes or less)”
Part 2: “How to choose (and use) a password manager”
Part 3: “Multi-factor authentication is easier than you think”
Part 4: “Do you need advanced security options?”
* The Amazon product is an affiliate link. I receive a small commission if you make a purchase from this source.